Integrate Yeastar P-Series Cloud Edition with Microsoft Entra ID
This topic describes how to integrate Yeastar P-Series Cloud Edition with Microsoft Entra ID (Azure Active Directory) .
Requirements
| Item | Requirement |
|---|---|
| Microsoft Entra ID | Free, Office 365 apps, Premium P1, or Premium P2 |
| Yeastar PBX Server |
Version 84.21.0.66 or later |
Prerequisites
Before you begin, make sure the followings are ready:
- Your organization already has a Microsoft Entra tenant.
- Use a Microsoft account with Global Administrator privilege to implement the integration.
Procedure
- Step 1. Obtain redirect URIs from PBX
- Step 2. Register an application in Microsoft Entra tenant
- (Optional) Step 3. Add SSO redirect URI to the Microsoft Entra application
- Step 4. Grant permissions to the Microsoft Entra application
- Step 5. Generate a client secret for the Microsoft Entra application
- Step 6. Connect PBX and Microsoft Entra ID
Step 1. Obtain redirect URIs from PBX
Obtain redirect URIs from Yeastar P-Series Cloud Edition, you will need the information when configuring a Microsoft Entra application for the integration.
- Log in to PBX web portal, go to .
- Click Integrate beside Microsoft 365.
- In the App Registration section, select and note down
the following redirect URIs.
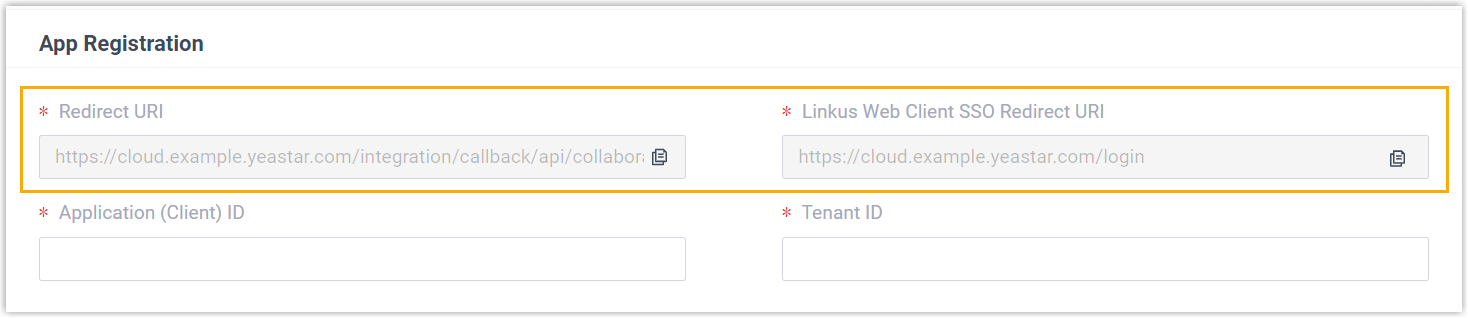
- Redirect URI: Used to specify the location to which you are redirected after the integration authentication is completed.
- Client SSO Redirect URI: Used to set up the Single Sign-on (SSO) feature of Linkus UC Clients.
Step 2. Register an application in Microsoft Entra tenant
Register a Microsoft Entra application that will be used to connect Yeastar P-Series Cloud Edition and Microsoft Entra ID.
- Log in to Microsoft Azure Portal with the Microsoft Global Administrator account.
- In the search bar, search and select Microsoft
Entra ID service to enter your organization's
directory.

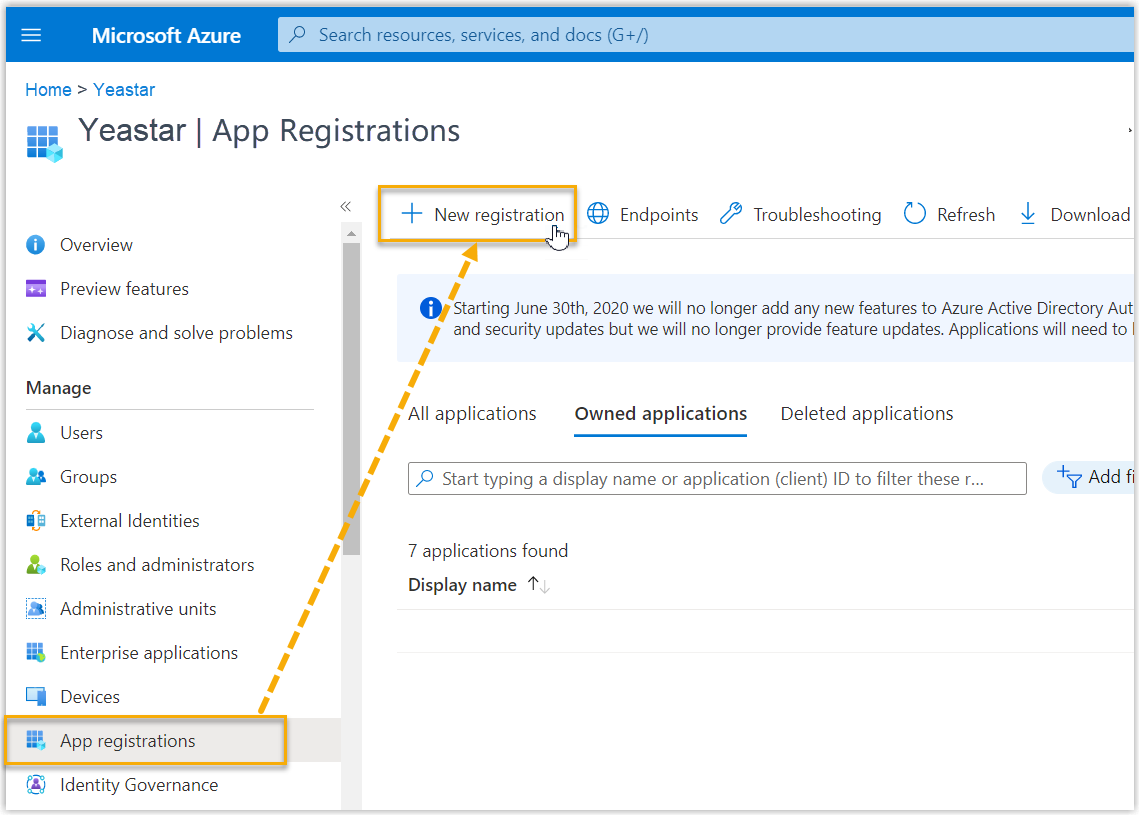
- On the left navigation bar of organization's
directory, go to App registrations, then click
New registration.
- In the Register an application page, do as
follows:
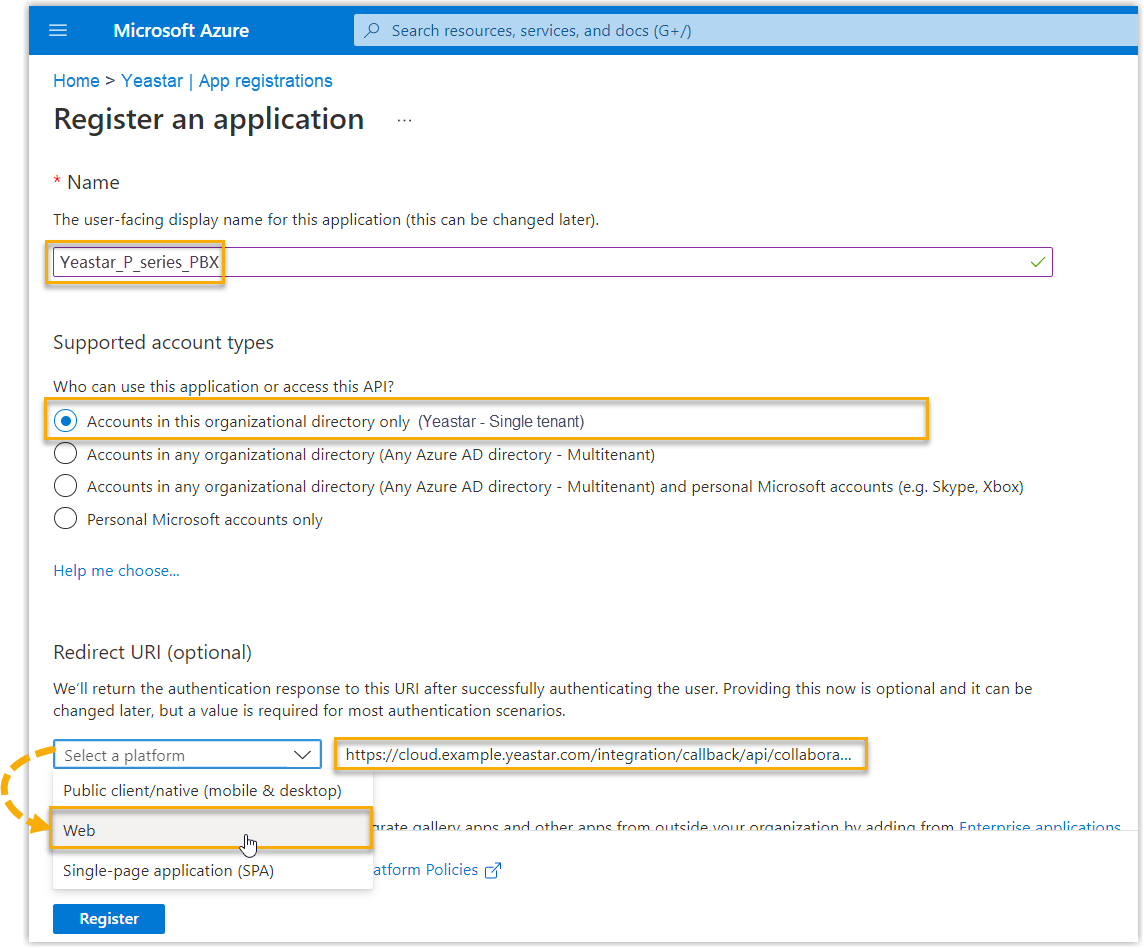
- Enter the registration information of the application.
- Name: Specify a name to help you identify the application.
- Supported account types: Select Accounts in this organizational directory only.
- Redirect URI: In the Select a platform drop-down list, select Web, then paste the Redirect URI obtained from the PBX.
- Click Register.
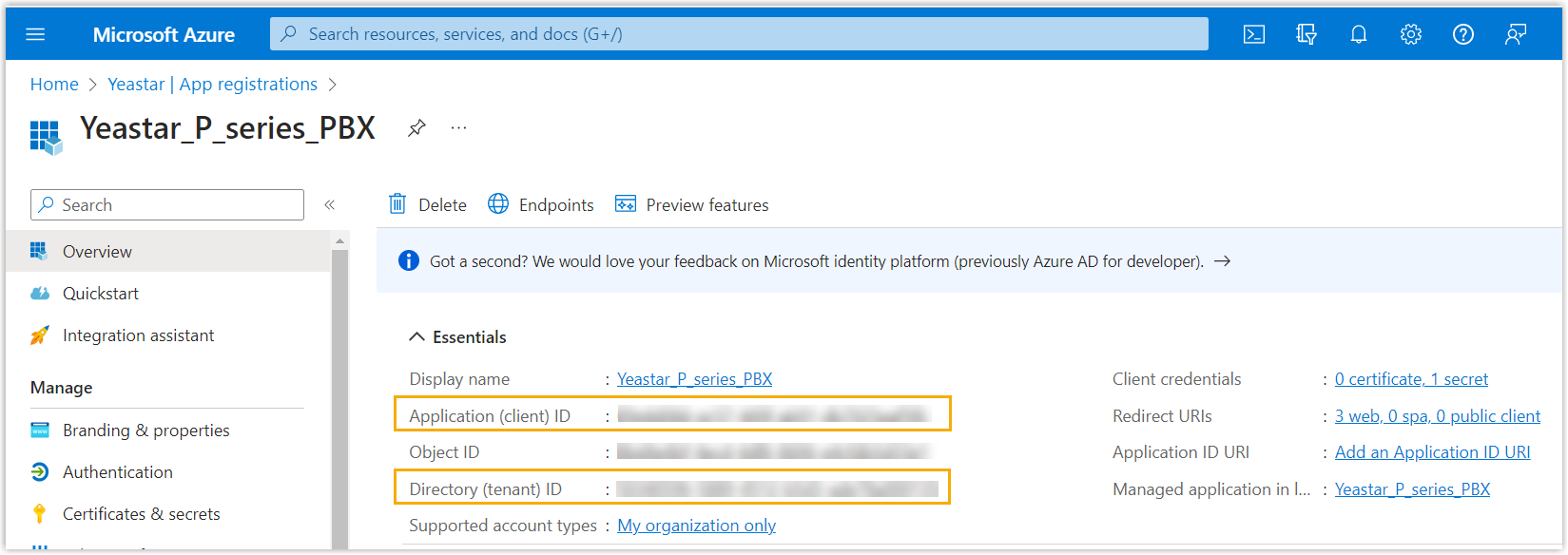
A Microsoft Entra application is registered successfully.
The Application (client) ID and Directory (tenant) ID of the application is displayed on the Overview page. Note them down as you will need to fill them into the PBX later.
- Enter the registration information of the application.
(Optional) Step 3. Add SSO redirect URI to the Microsoft Entra application
If you want to implement Single Sign-on (SSO) to allow the users synced from Microsoft Entra ID to log in to Linkus UC Clients by their Microsoft accounts, you need to add the Client SSO Redirect URI to the Microsoft Entra application.
- On the left navigation bar of the Microsoft Entra application, go to
Authentication.
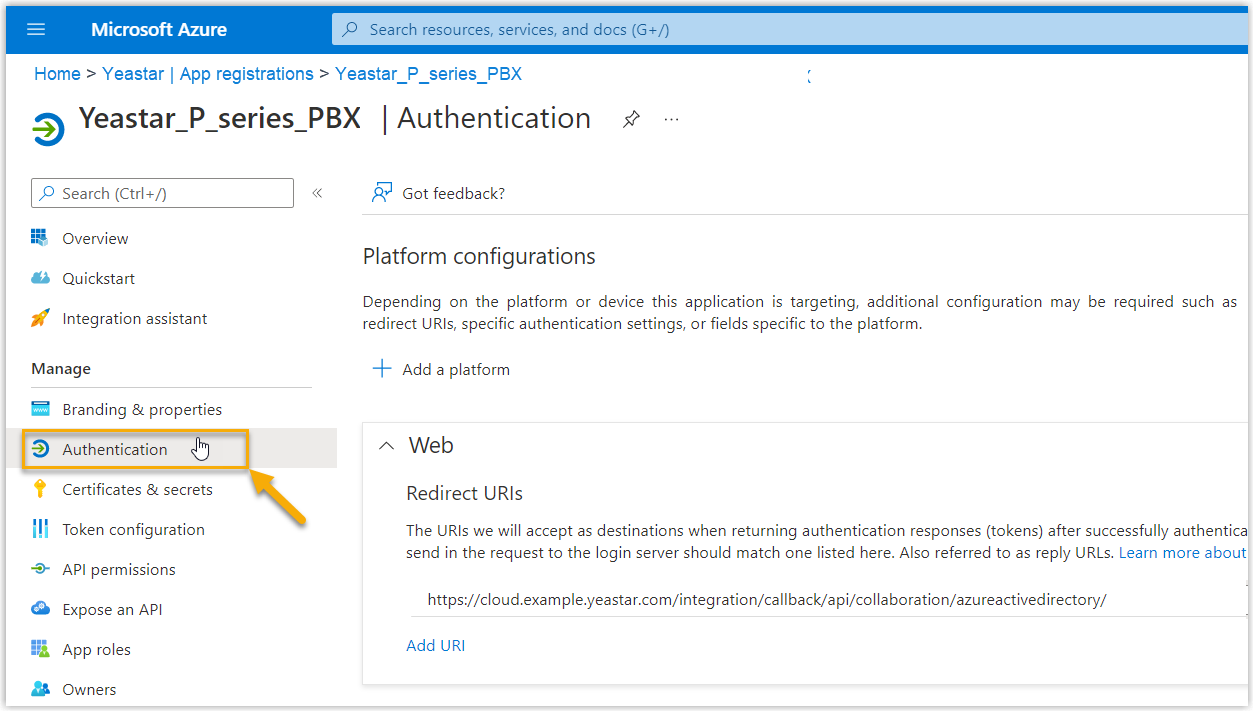
- Add the SSO Redirect URI of Linkus UC
Clients.
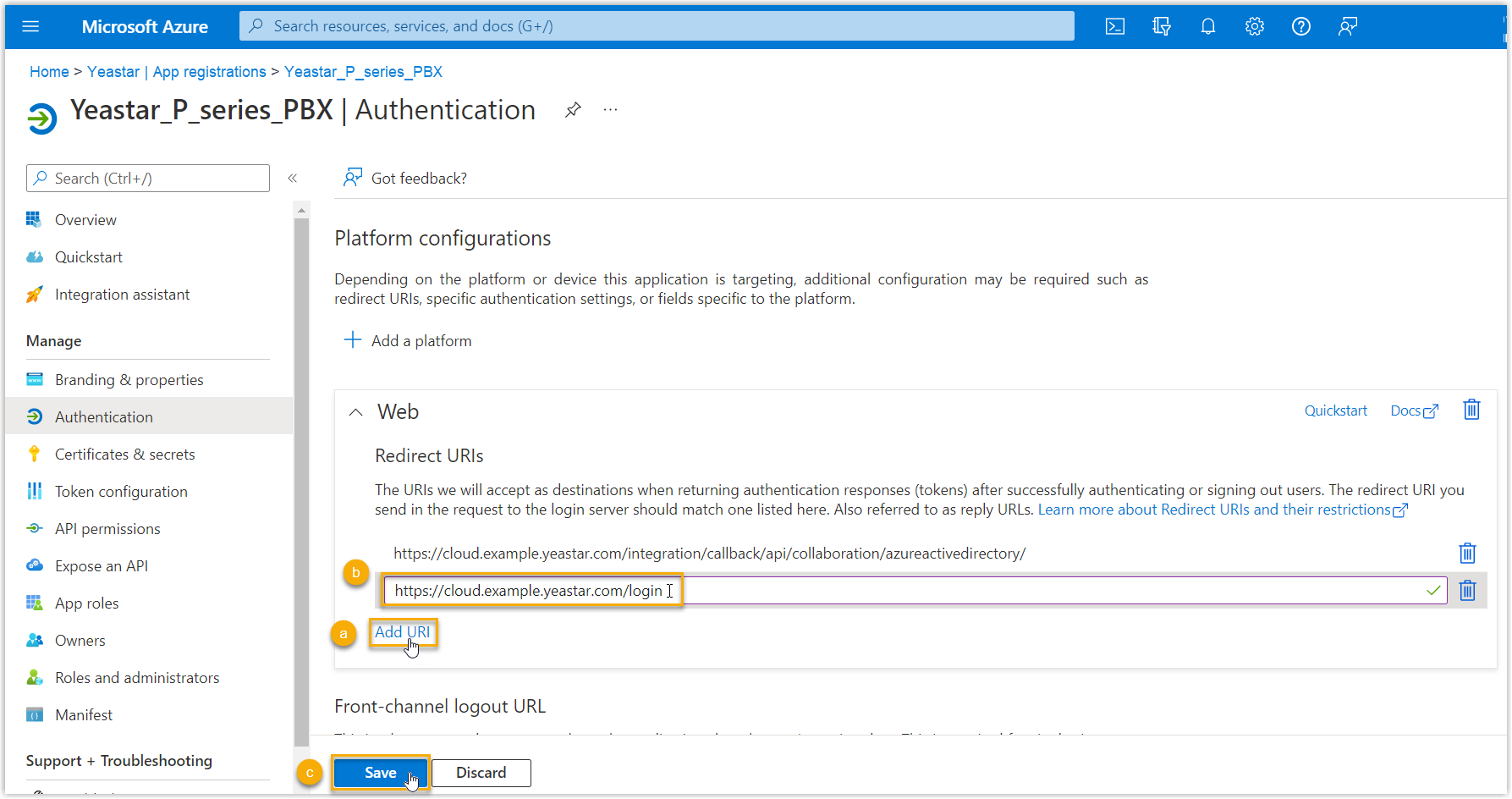
- On the Authentication page, click Add URI in the Web section.
- Paste the Client SSO Redirect URI obtained from the PBX.
- Click Save.
Step 4. Grant permissions to the Microsoft Entra application
- On the left navigation bar of the Microsoft Entra application, go to API
permissions, then click Add a permission.
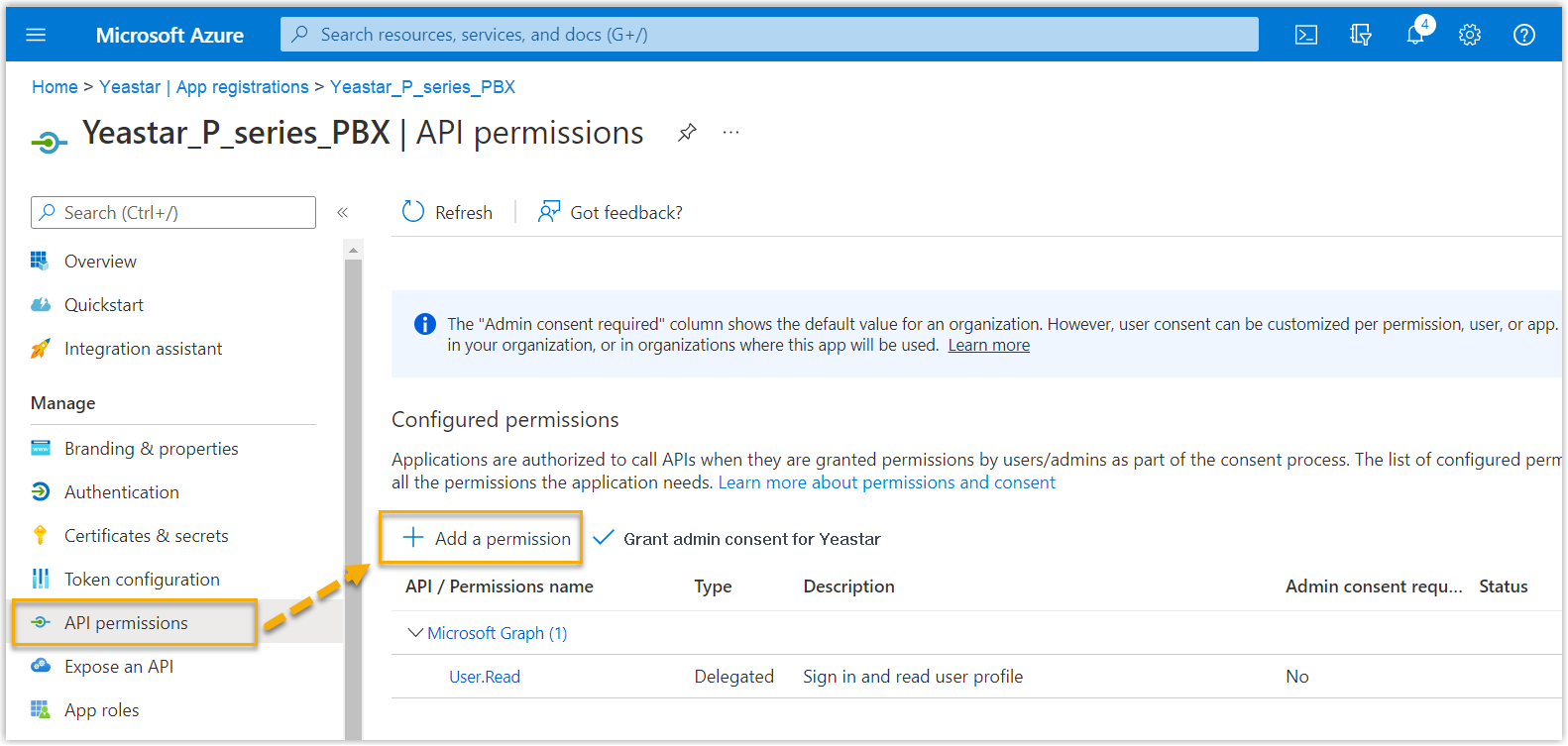
- In the Select an API page, go to .
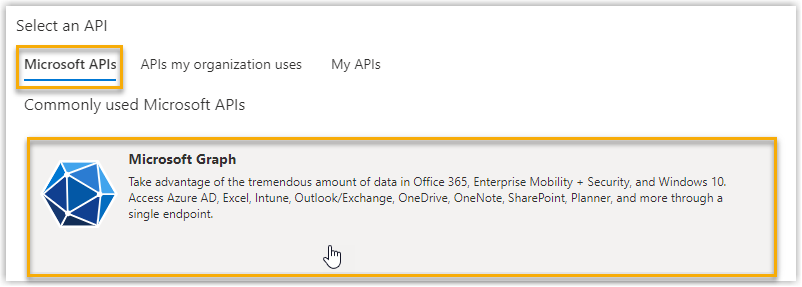
- Add the required permission to allow the application to set the state of
users' presence.
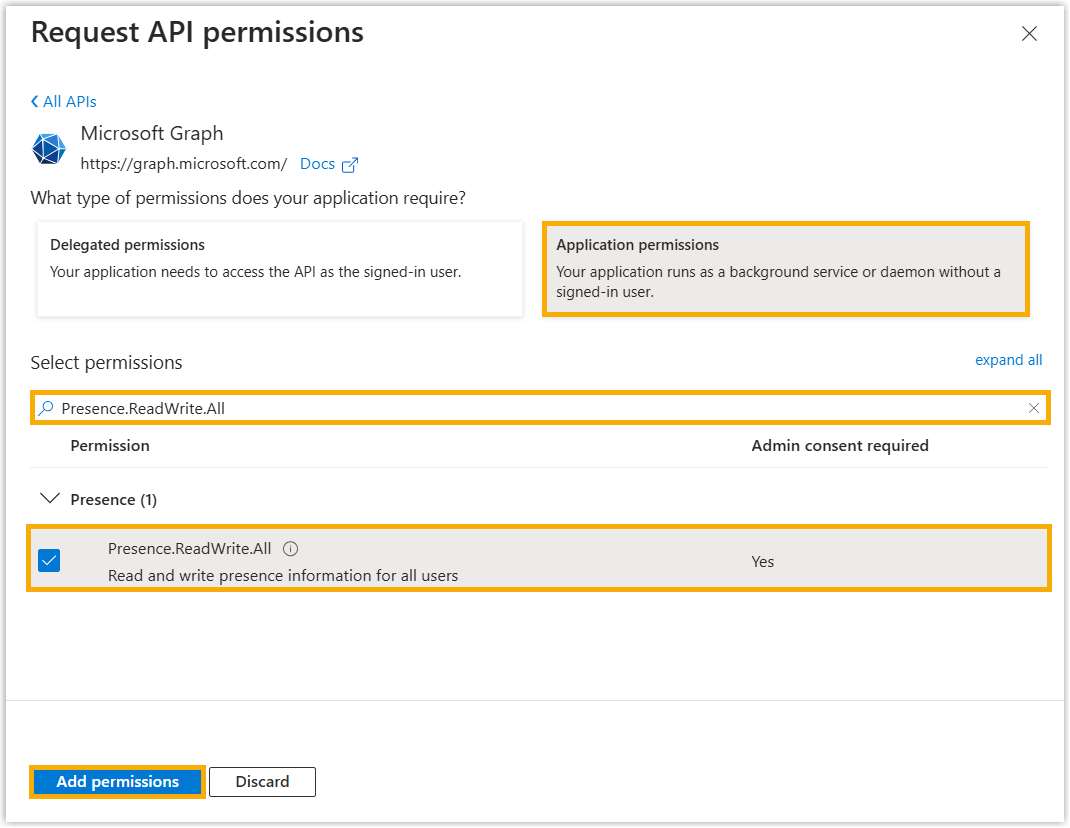
- Click Application permissions, search and
select Presence.ReadWrite.All permission,
then click Add permissions.
- Click Grant admin consent for... to grant the
permission to the application.
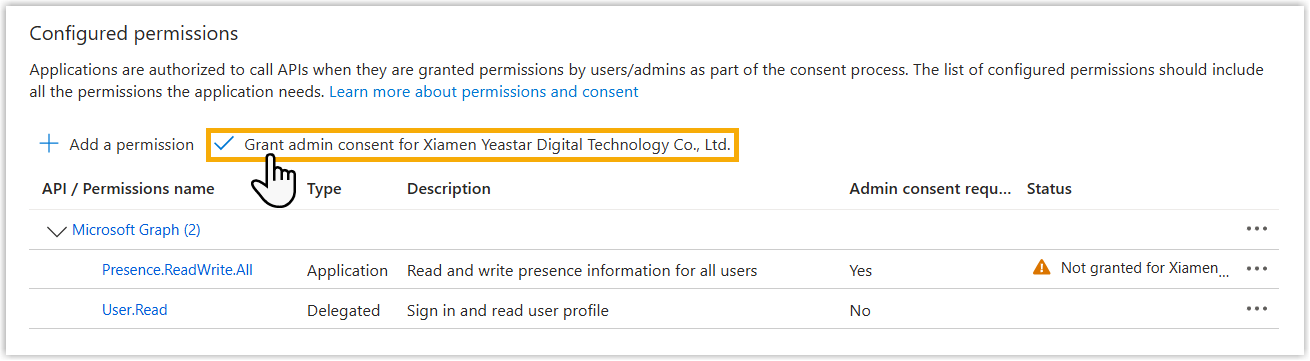
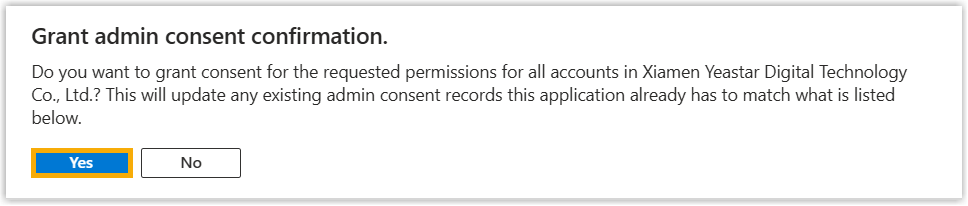
- In the pop-up dialog box, select
Yes.
The Status of the permissions changes to
 , indicating that the API permission
has been granted to the application successfully.
, indicating that the API permission
has been granted to the application successfully.
- Click Application permissions, search and
select Presence.ReadWrite.All permission,
then click Add permissions.
Step 5. Generate a client secret for the Microsoft Entra application
Generate a client secret for the Microsoft Entra application to authenticate the application in the integration.
- On the left navigation bar of the Microsoft Entra application, go to , then click New client
secret.
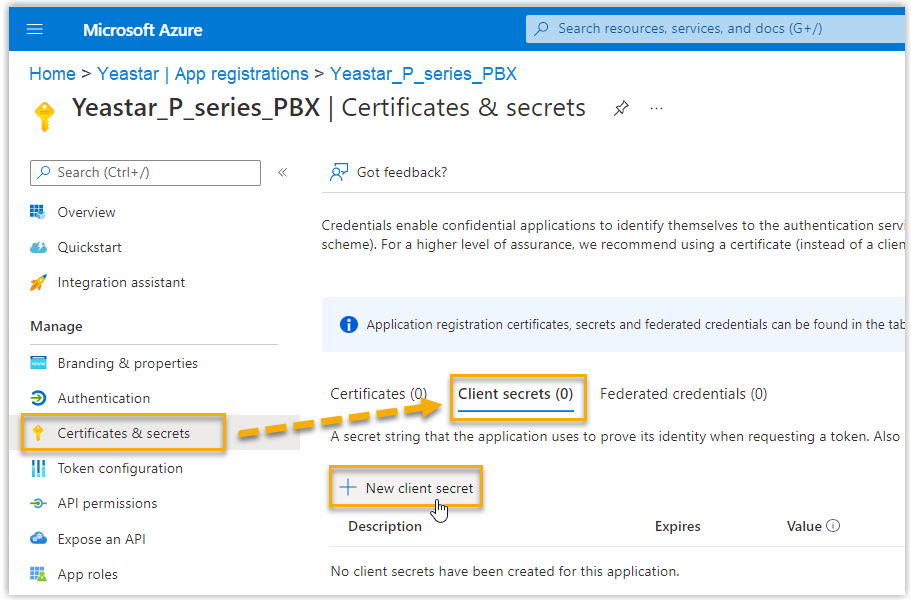
- In the Add a client secret page, do as follows:
- Add a description and set an expiration date for the client
secret.
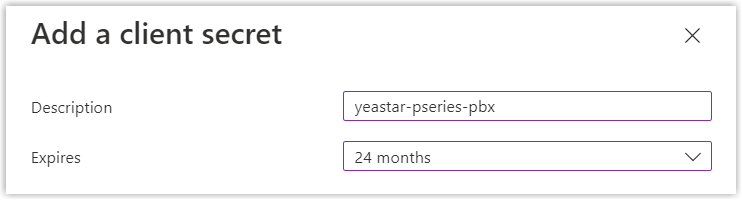
- On the bottom of the page, click Add.
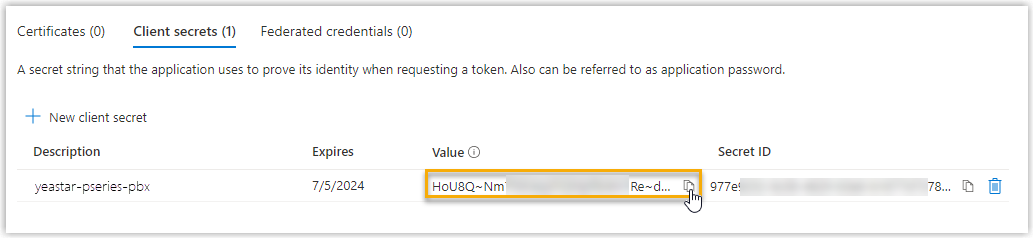
A client secret is created and displayed in the Client secrets list.
- Add a description and set an expiration date for the client
secret.
- Note down the client secret's Value
as you will need to fill it into the PBX later.Important: Record the client secret's value before leaving the page, as the key is only shown once. Otherwise, you will have to create a new secret.
Step 6. Connect PBX and Microsoft Entra ID
Fill the application ID and client secret gathered from the Microsoft Entra application into PBX to implement the integration between Yeastar P-Series Cloud Edition and Microsoft Entra ID.
- Log in to PBX web portal, go to .
- Click Integrate beside the Microsoft 365 service.
- In the App Registration section, enter the following
information:
- Application (Client) ID: Paste the application ID.
- Tenant ID: Paste the tenant ID.
- In the Certificates & Secrets section, paste the client secret in the Client Secret field.
- Click Save.
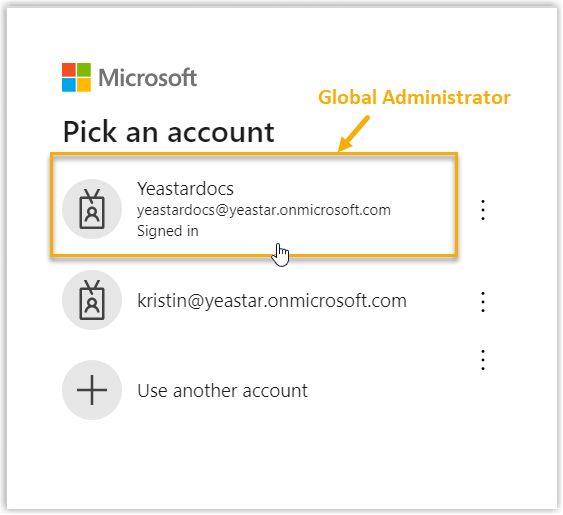
You are redirect to the Microsoft Sign-in page.
- Sign in with the Microsoft account that has
Global Administrator privilege.
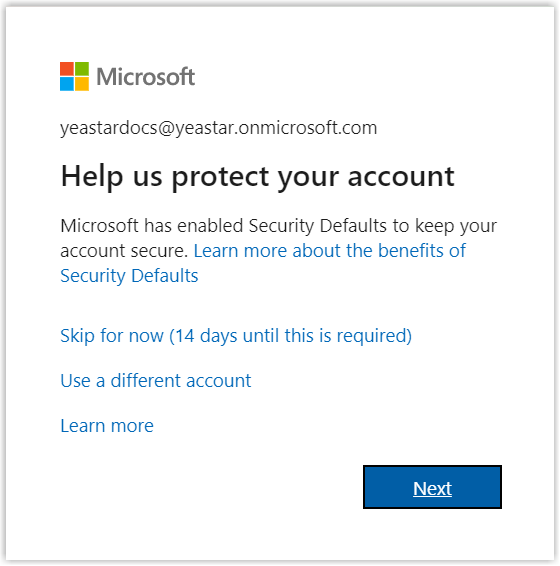
- You might be asked to provide an additional security confirmation. Click
Next to complete it or skip for now.
-
In the pop-up window, check the permissions and click Accept to confirm.
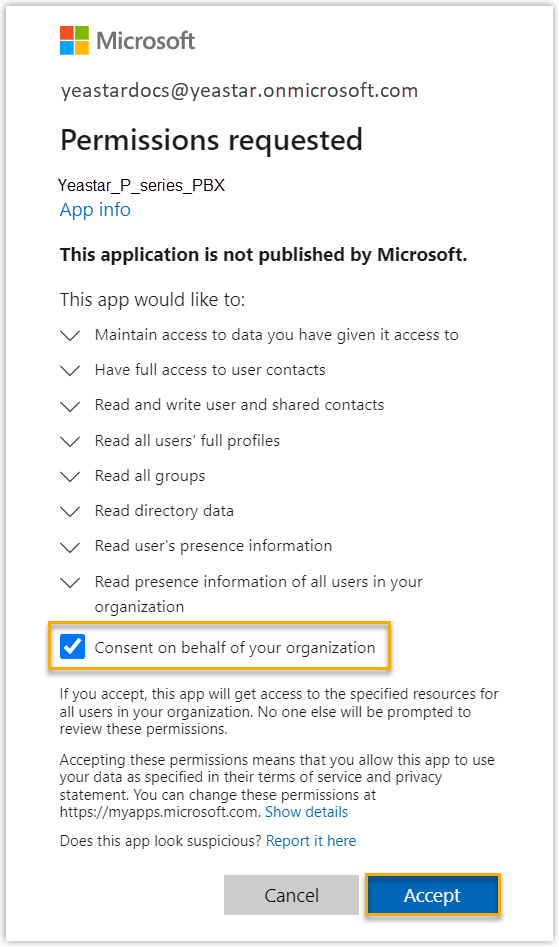
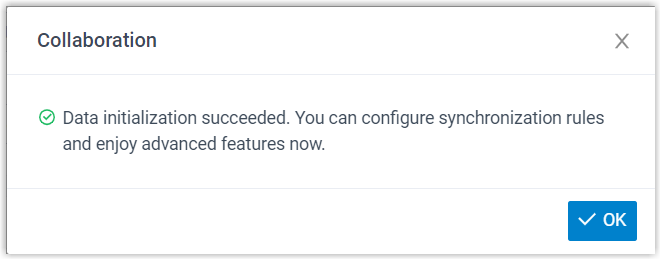
- On the PBX configuration page, click OK to close the
dialog box.
Result
The status of the integration displays Connected, indicating that the PBX is successfully connected to your organization's Microsoft Entra ID.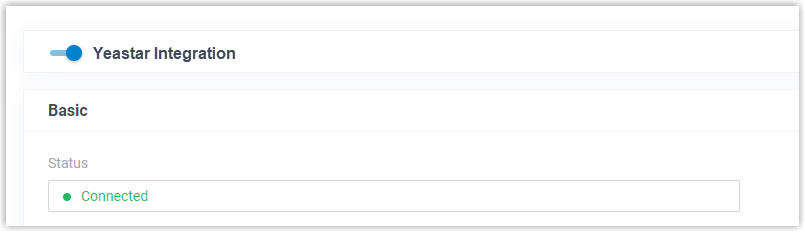
What to do next
Set up synchronization rules to synchronize the desired users and groups from Microsoft Entra ID to PBX. For more information, see the following topics: