Yeastar P-Series Cloud Edition Security Guide
Attacks on PBX system can come from the Internet or telephone lines. Fraudsters always try every means to exploit vulnerabilities to gain access to phone system and make fraudulent calls. As a result, fraudsters take revenues generated from these calls, while you get a costly telephone bill. The Security Guide is intended to elaborate on how to protect your PBX system from security breaches and mitigate the threat of toll fraud.
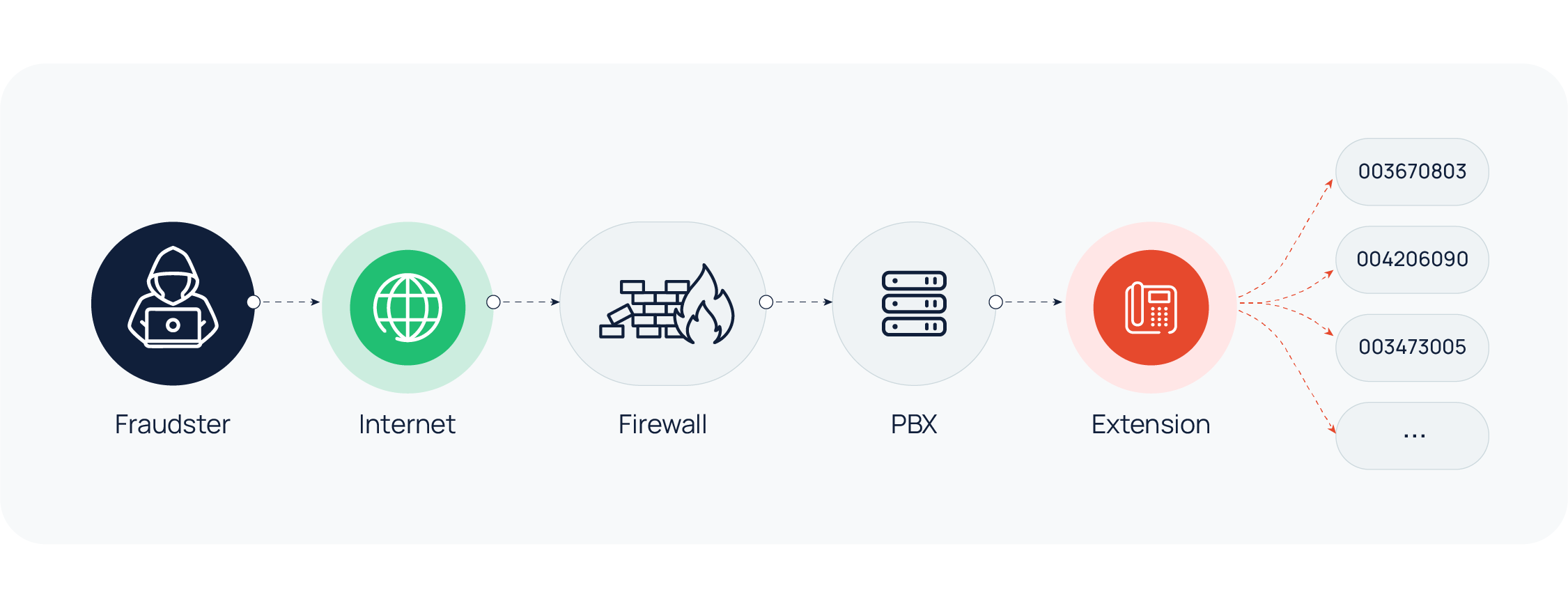
How do fraudsters get access to a PBX?
Typically, fraudsters use vulnerability scanners to crawl the Internet looking for vulnerabilities in your company's firewalls (like open ports). If any open port is detected, the fraudsters may punch requests at the port in order to tease out information about system vulnerabilities. In the end, they may have all the information they need to brute force their way through the firewall. Once the firewall has been breached, the fraudsters can gain access to the PBX, build a back door into the system, and use it to route as much traffic as they want, eventually leading to toll fraud.
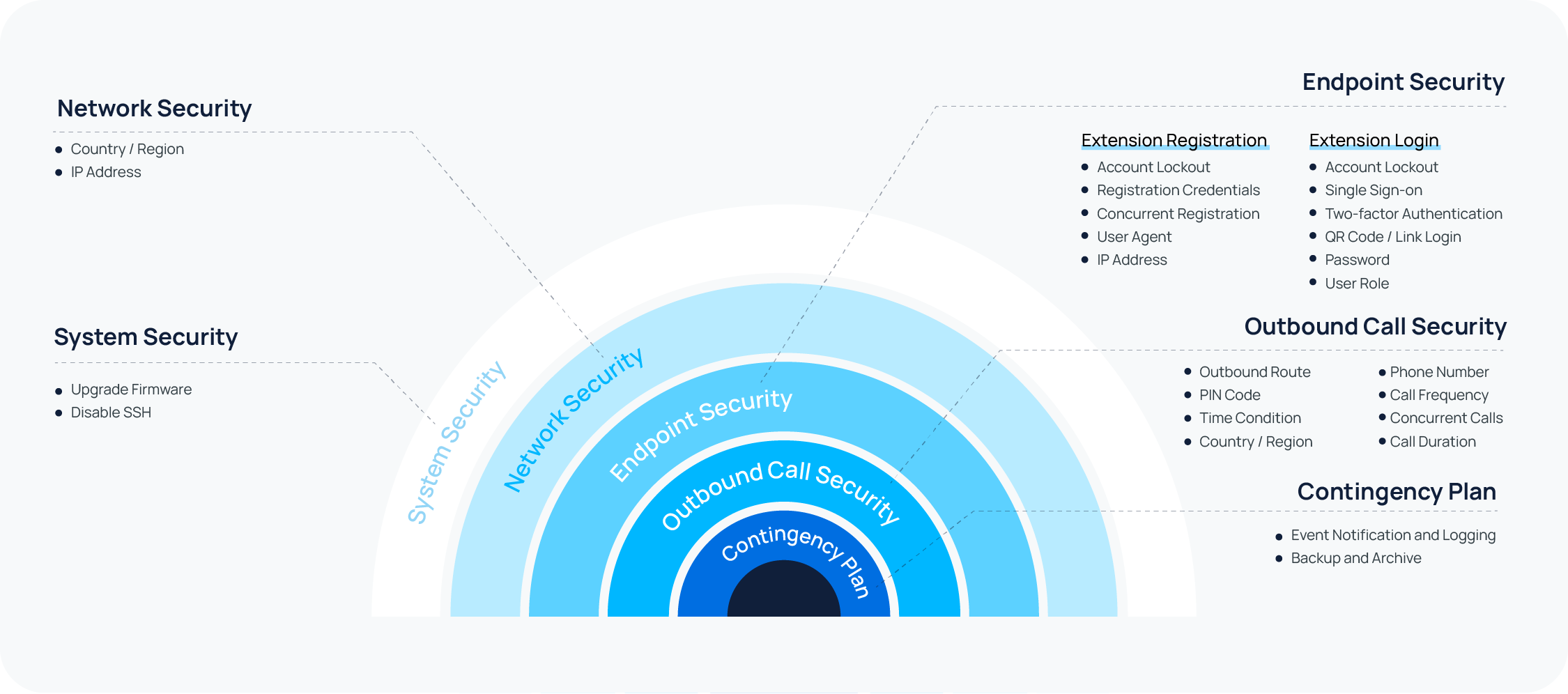
How to protect PBX from security breaches and toll fraud?
Actually, vulnerabilities in your phone system can not be eliminated due to the ever-changing need of your business communications and ever-evolving of hacking techniques. However, you can reduce the vulnerabilities with better awareness, proactive actions, and regular audit.
To maintain a high level of security, we recommend that you adopt a multi-layered security strategy. This involves integrating several protective mechanisms to shield the system from security threats. Even if one defense layer gets compromised, others remain in place to offer security.