Network Security
Network Security is the second line of defense in multi-layered security strategy, monitoring access to your phone system, accepting or denying access based on a set of pre-defined rules. You can enhance network security by utilizing Remote Access Service, Global Anti-hacking IP Blocklist, Allowed Country IPs, Static Defense, and Auto Defense policies.
Avoid Port Forwarding for Remote Access
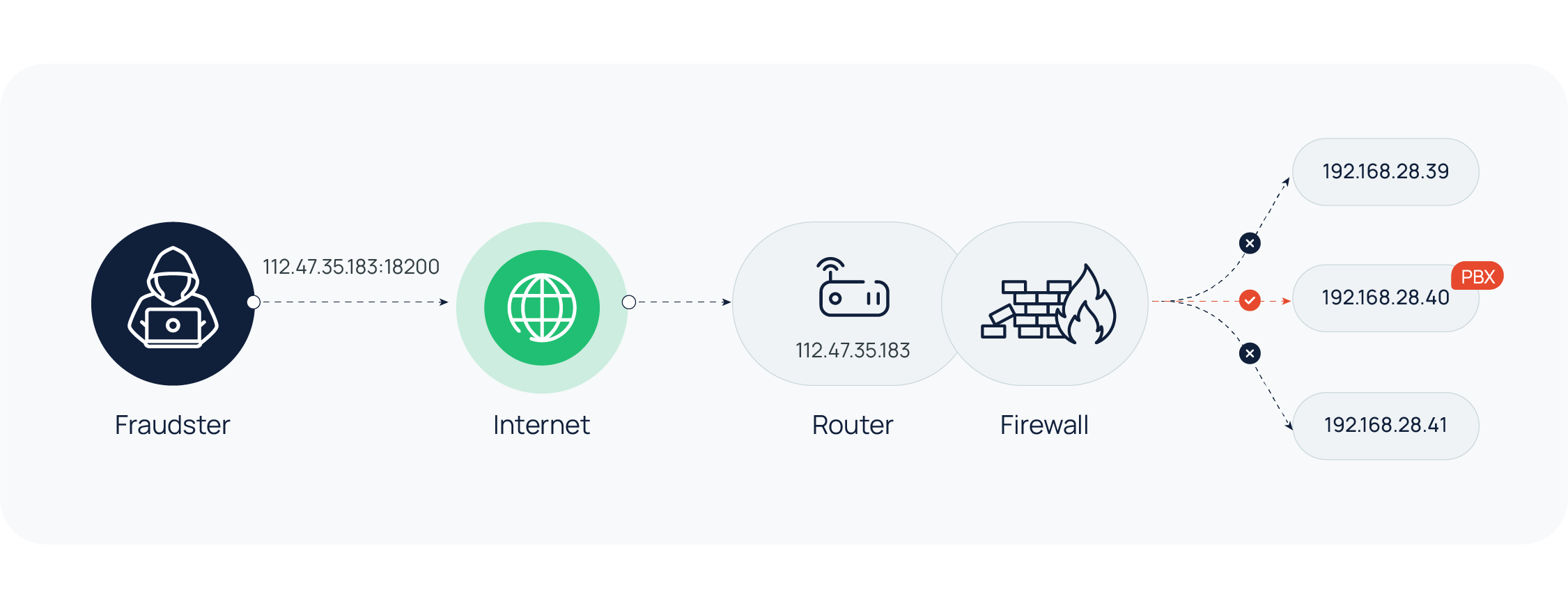
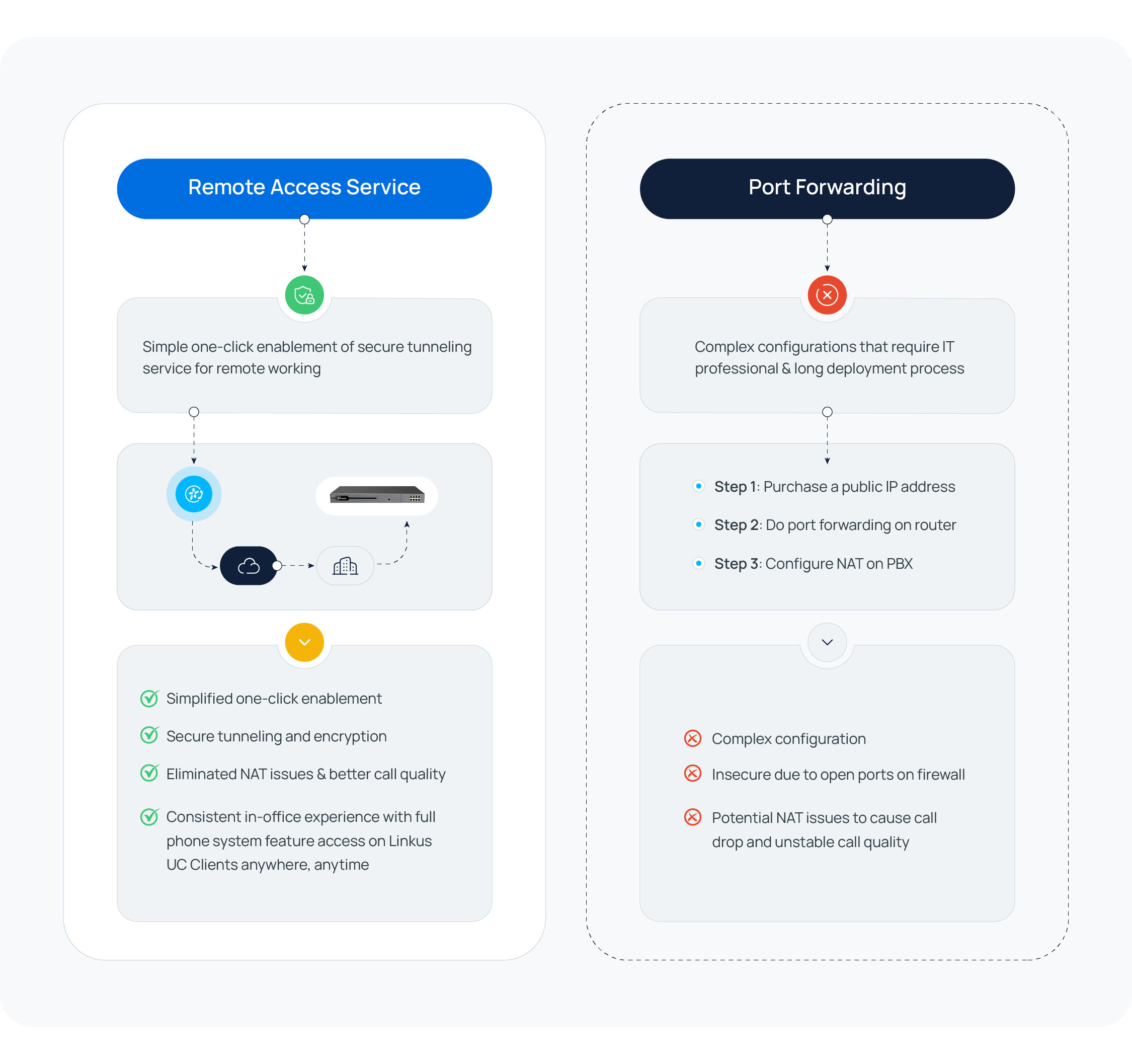
In an attempt to offer remote access for remote and mobile users, most on-premises PBX providers will recommend Port Forwarding. Essentially, Port Forwarding maps an external port on your public IP address to the PBX that is within your Local Area Network (LAN). This exposes your PBX on the Internet and brings potential risks, because hackers could penetrate your network through the forwarded port.
Yeastar P-Series Software Edition supports Remote Access Service (RAS), which allows for remote access without port forwarding. It provides an easy-to-access domain name for you to customize your PBX URL and allows you to perform daily business communications and administration with Linkus UC Clients anywhere. Moreover, RAS offers advanced access control to ensure further security. You can permit or block remote access for SIP registration, web, Linkus, LDAP, and API, customize remote access authorization by extension or department, and apply IP restriction to further secure all the remote access.
Restrict Access to PBX by Yeastar-Shared IP Blocklist
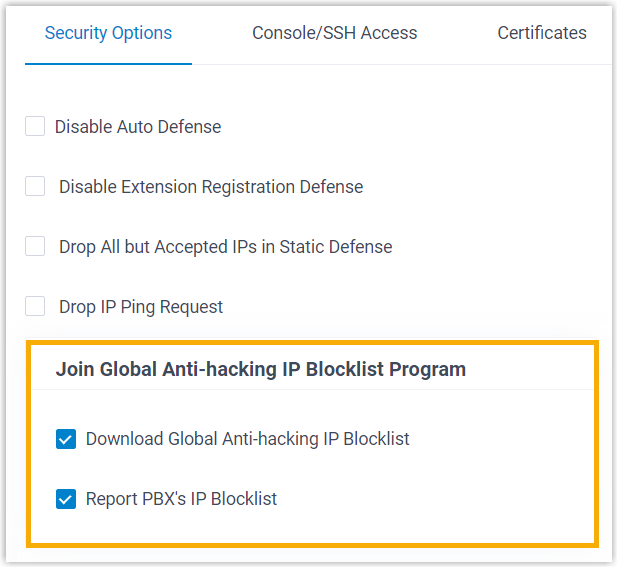
Yeastar launches a Global Anti-hacking IP Blocklist Program, which centrally records a wide range of IP addresses that have been blocked by Yeastar PBXs worldwide and that are suspected of malicious activity or attack.
The IP blocklist is shared among all the Yeastar PBXs. With the Yeastar Global Anti-hacking IP Blocklist, all connections to your PBX from the IP addresses in the blocklist will be dropped, thus reducing the risk of cyber attacks.
Go to to double check that you have participated in the program.
Restrict Access to PBX by Country/Region
Implement geographic restrictions to limit access to Yeastar P-Series Software Edition from specific countries or regions. PBX will only allow access from your trusted geographic locations while blocking all other traffic.
To set up geographic restrictions, follow the instructions below:
- Go to .
- Turn on the switch of Enable Allowed Country/Region IP Access
Protection.Important: If a pop-up appears, you MUST confirm to allow access from your country or region, or you will NOT be able to access your system.
- At the top-right search bar, search the country or region that you want to
grant access, then turn on the switch in the
Operations column.
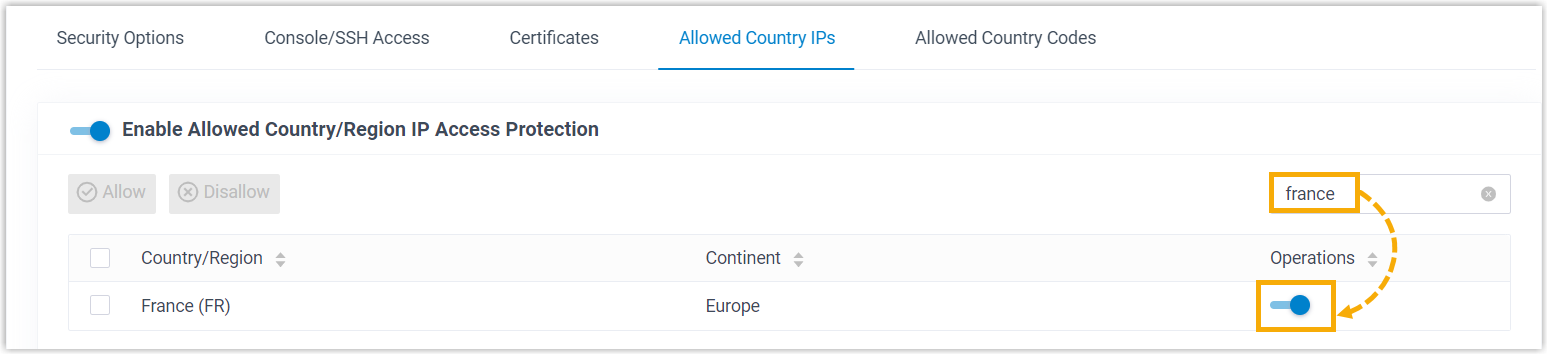
- Click Apply.
Restrict Access to PBX by Static Firewall Rules
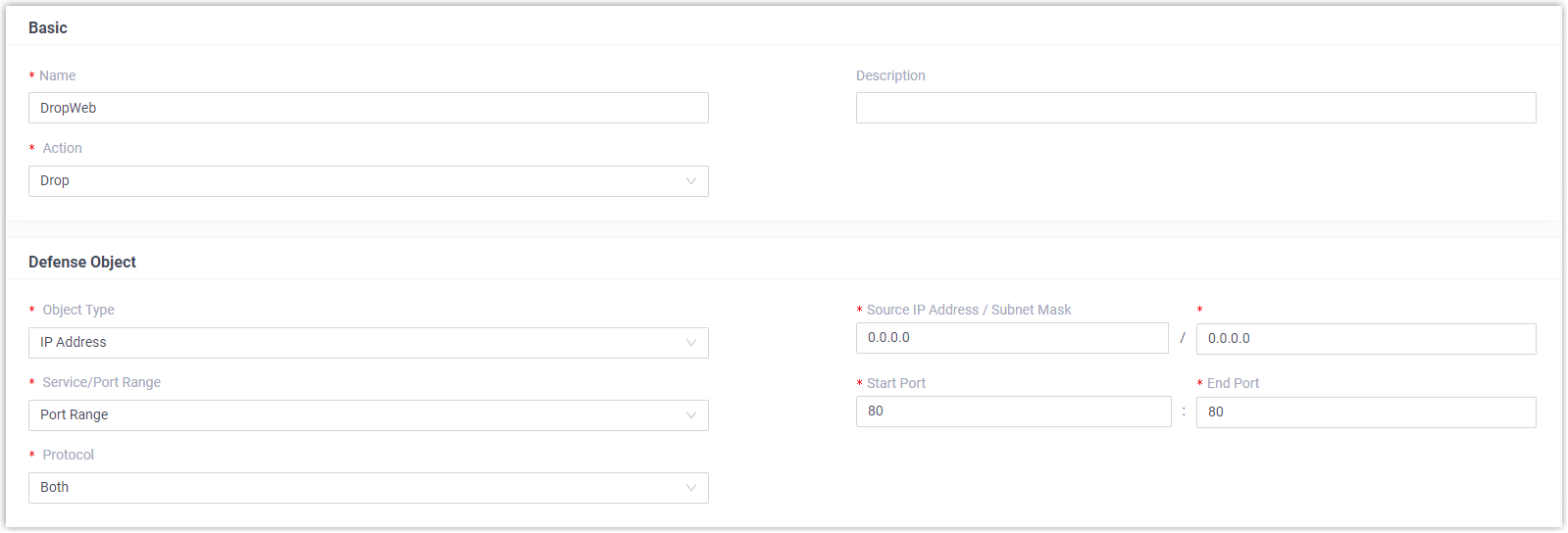
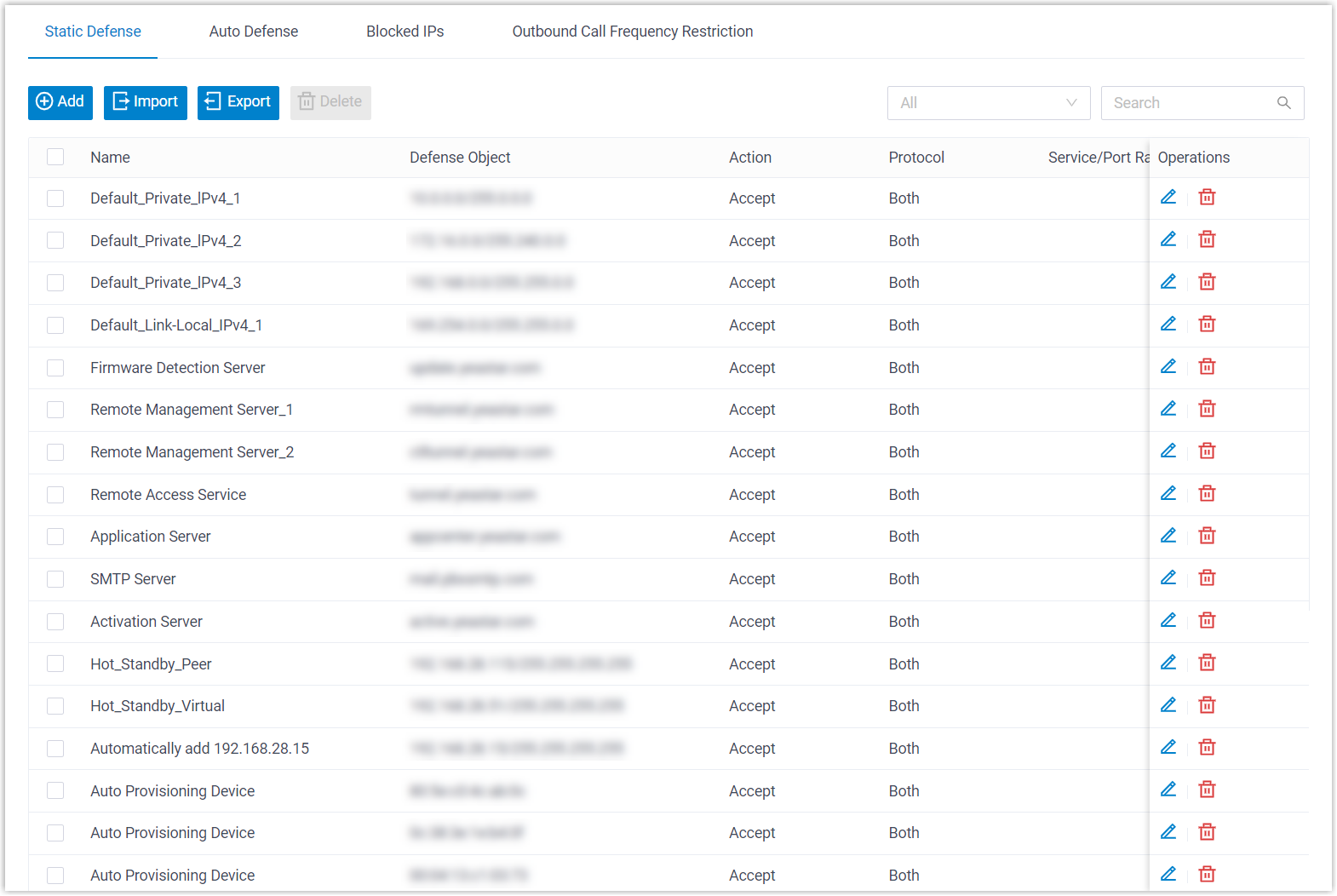
Static Firewall Rules can monitor and control incoming traffic based on IP address, domain name, or MAC address, effective in protecting trusted connections and blocking known threats. There are default rules to accept access from your LAN, auto-provisioned devices, and Yeastar services. You can also add custom rules to Accept, Drop, or Reject specific traffic.
Go to to check the default rules and add custom rules as needed.
- Default Static Defense Rules
- Examples of Custom Static Defense Rule
-
Table 1. Example 1: Accept remote registration from a trusted IP address Scenario Setting Add a static defense rule to allow remote registration to Yeastar PBX.
For example, the trusted IP address is
110.30.25.152.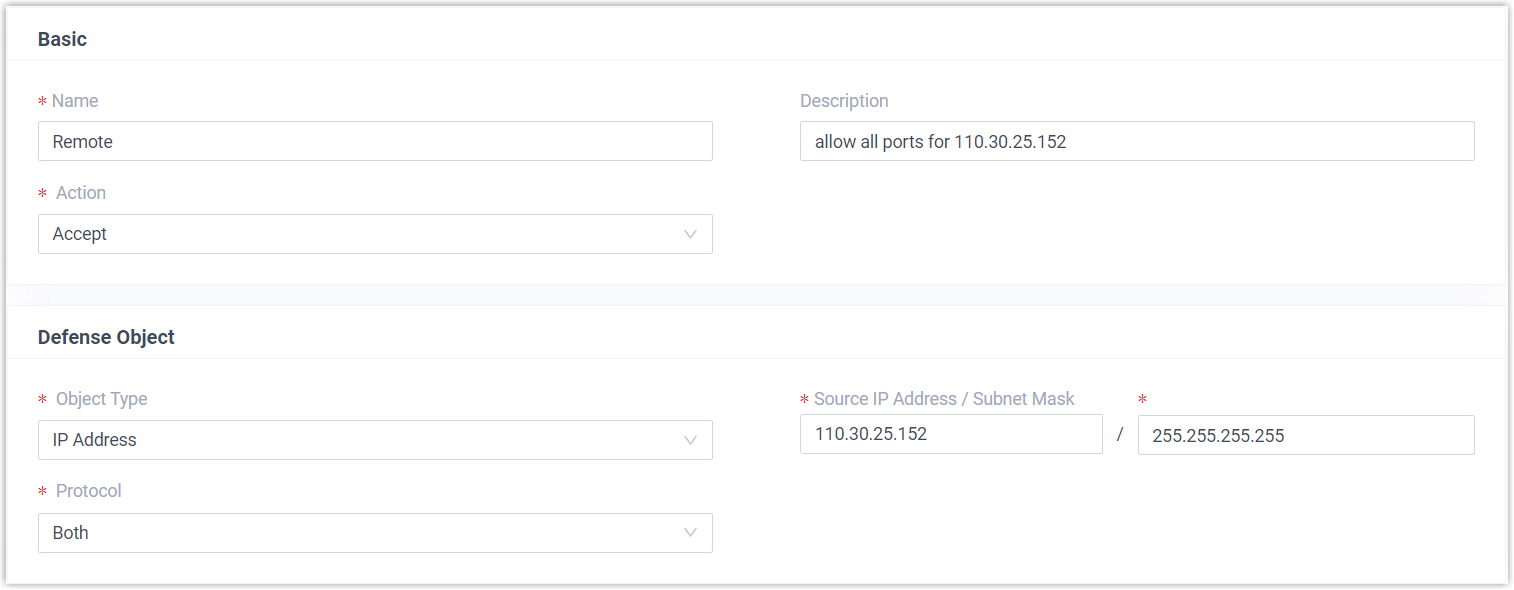
Restrict Access to PBX by Dynamic Firewall Rules
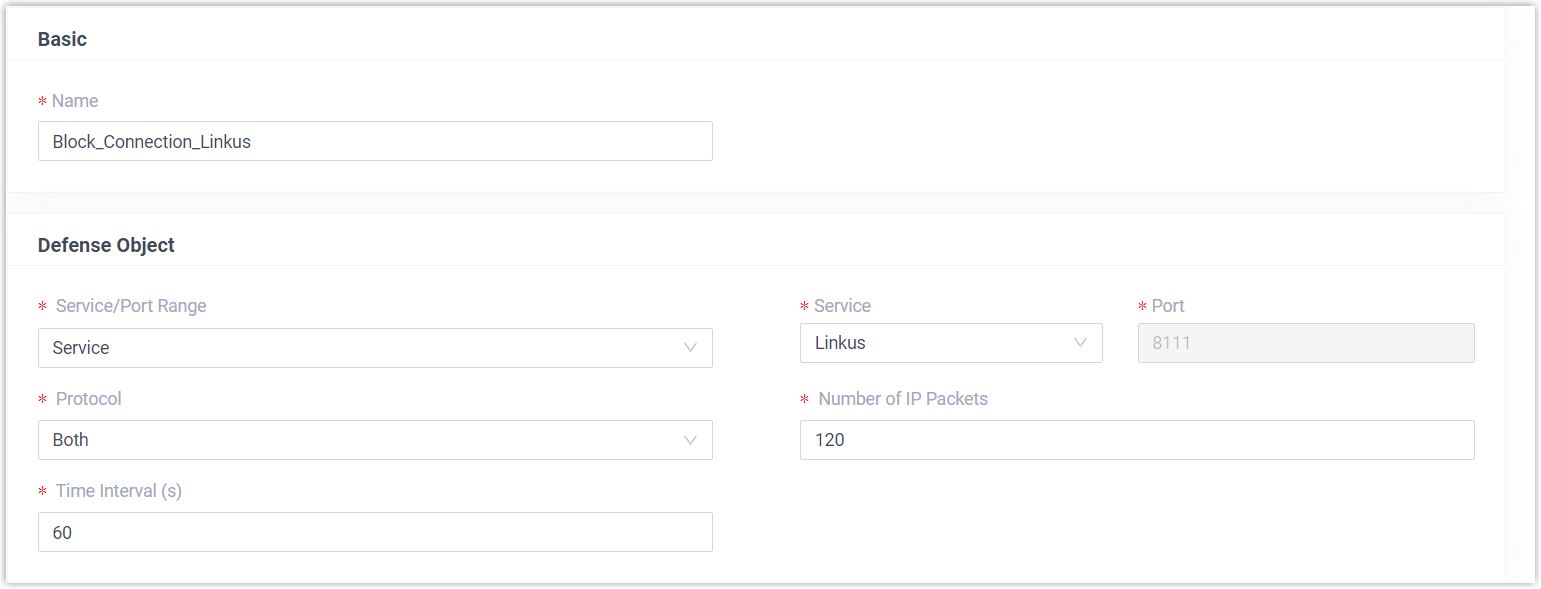
Dynamic Firewall Rules can block unknown threats by monitoring the packets sent within a specific time interval, effective in preventing massive connection attempts or brute force attacks. Yeastar P-Series Software Edition has default auto defense rules to protect security of SSH connection, SIP registration, and web access. You can also add custom rules to strengthen the security.
- Default Auto Defense rules
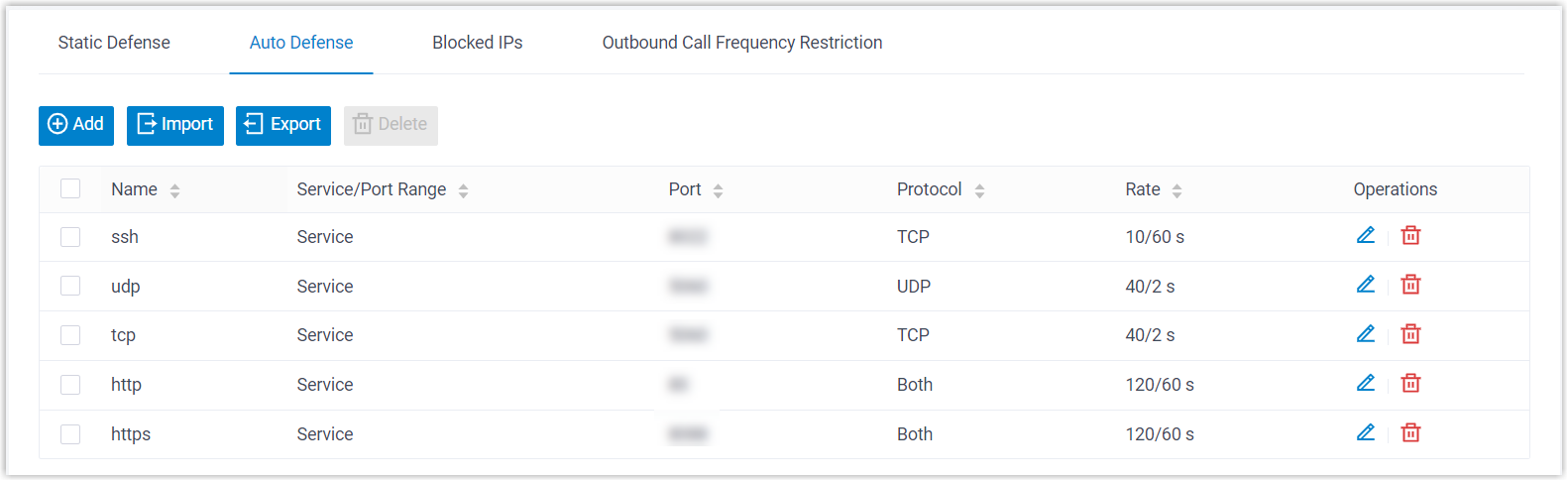
- Example of Custom Auto Defense Rule
-
Table 3. Example: Block connections to Linkus Scenario Setting Add a rule to block connections to Linkus if an IP address sends more than 120 packets in 60 seconds.