Build up the OpenVPN Server
Step 1. Configure the OpenVPN server
- Log in the PBX web interface, go to VPN Server, check the option Enable VPN Server.
- Configure the OpenVPN server settings.
Here is an example of OpenVPN server settings:
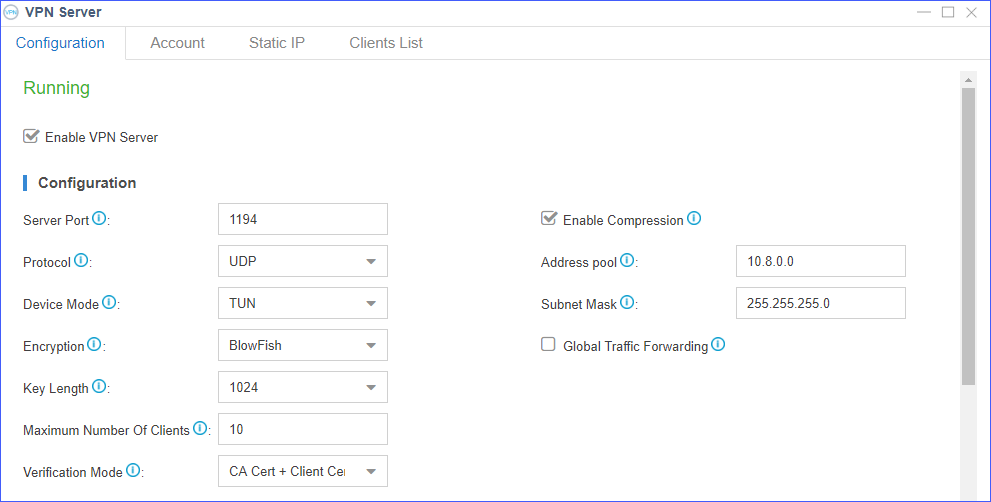
Table 1. Description of OpenVPN settings Options Description Server Port Specify which TCP/UDP port should OpenVPN listen on. The default port is 1194.
Protocol Choose the protocol. - TCP
- UDP
Device Mode Choose the device mode:
- TUN: a TUN device is a virtual point-point
IP link.
If you choose TUN mode, you should allocate a static IP address for windows client because of TAP-WIN32 driver limitation.
- TAP: a TAP device is a virtual Ethernet adapter.
Android and iOS clients don’t support TAP mode.
Note: If Android, iOS, and other clients need to access to the PBX via OpenVPN network at the same time, we recommend that you use the TUN mode.Encryption Choose encryption method. - BlowFish
- AES-128
- AES-256
- Triple-DES
Key Length Set the key length. Note: The value must be the same asKEY_SIZEwhich were set in the vars.bat file.Maximum Number of Clients Set the maximum number of clients that could connect to the OpenVPN server. Verification Mode Choose the Verification Mode of Client. - CA Cert + Client Cert (recommend)
- CA Cert + Client Cert + Account & Password
- CA Cert + Account & Password
Note: If you choose CA Cert + Client Cert + Account & Password or CA Cert + Account & Password, you need to configure OpenVPN username/password authentication for each client later.Enable Compression Whether to compress the VPN link. Address pool Define the address pool. Subnet mask Set the subnet mask. Global Traffic Forwarding If enabled, the client will configure a default gateway to the server after the connection is successful, and all the traffic will be forwarded by the server. (The OpenVPN server machine may need to NAT or bridge the TUN/TAP interface to the internet in order for this to work properly). If disabled, only the communication data with the server will go through VPN tunnel, other traffic will go through the original forward routing.
This feature may not take effect on some clients.
- Upload certificates and keys for server.
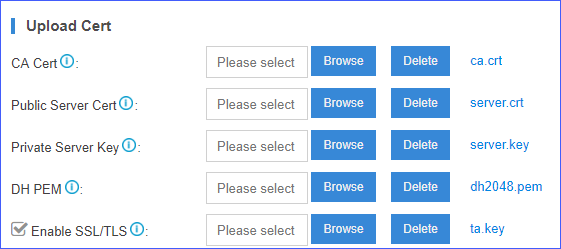
Table 2. Options CA & Key CA Cert Upload ca.crt. Public Server Cert Upload the OpenVPN server certificate server.crt. Private Server Key Upload the OpenVPN server key server.key. DH PEM Upload the Diffie Hellman file dh2048.pem. Note: If theKEY_SIZEis 1024, then upload the file dh1024.pem.Enable SSL/TLS Enable SSL/TLS on the VPN server, and then upload ta.key file. - Click Save and Apply.
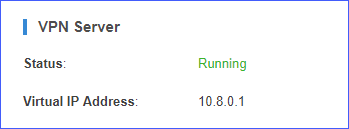
Step 2. Check the VPN server status
- Go to ,
check
the OpenVPN status and virtual IP address.
Step 3. Forward VPN server port
To ensure that VPN clients can access the PBX, you should forward VPN server port on your router. The default VPN server port is 1194.
Note down the public IP address of PBX and the external VPN server port. Later, you need to enter the remote IP address and remote server port in the client configuration file.