Authorization Rules
Yeastar Workplace API utilizes OAuth 2.0 for authorization, granting third-party applications access to resources on Yeastar Workplace through secure tokens, eliminating the need for user credentials. This topic explains the authorization process and the token validity period.
Authorization process
The process that a third-party application accesses the Yeastar Workplace API using OAuth2.0 is shown below.
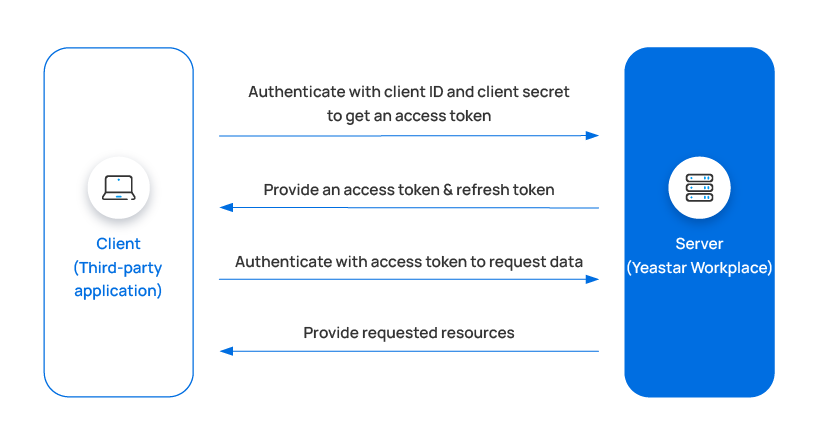
- Third-party application uses the credentials (Client ID and Client Secret) obtained from Yeastar Workplace admin portal to request an access token, which is required for the application to access Yeastar Workplace API.
- Yeastar Workplace validates the credentials, and sends an access token along with a refresh token.
- Third-party application calls the Yeastar Workplace API by passing the
access token either in an
AuthorizationHTTP headerBearervalue or in anaccess_tokenquery parameter. - Upon receiving the request, Yeastar Workplace authenticates the access token and returns a response, providing the information requested by the API call.
- Access token expires 24 hours after it is issued, you need to refresh the access token before it expires.
Token validity period
Both the access token and refresh token are valid for 24 hours.