Authorization Rule
Yeastar P-Series PBX System API uses the OAuth 2.0 protocol for authentication and authorization. This topic introduces the authorization process and the token expiration time.
Authorization process
The process that a third-party application accesses the Yeastar P-Series PBX System API using OAuth 2.0 is shown below.
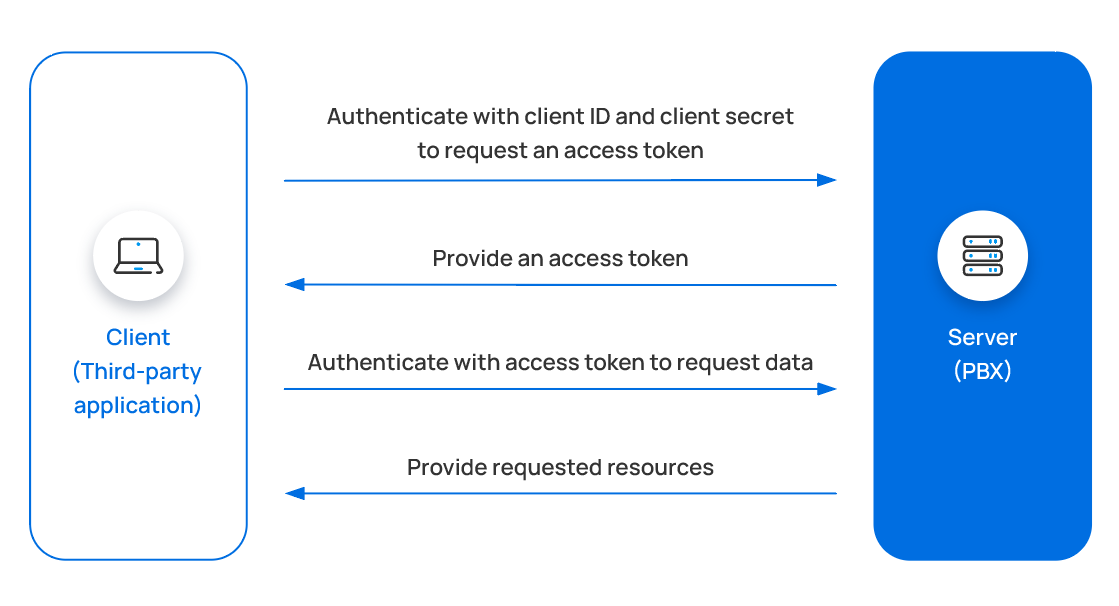
- Third-party application authenticates with credentials to request an
access token.
After an application obtains credentials ( Client ID and Client Secret) from the PBX web portal (Path: ), the application sends the credentials to request an access token.
- PBX provides an access token.
The PBX validates the Client ID and Client Secret, and responds with an access token.
- Third-party application uses the access token to call an API.
The third-party application sends API requests carrying the obtained access token to make authenticated API calls.
- PBX provides requested resources.
The PBX authenticates the access token and returns the requested data.
- Refresh the access token if necessary.
The access token expires after 30 minutes. You can refresh access token to obtain a new access token for API calls.
Token expiration
The access token expires after 30 minutes, and the refresh token expires after 24 hours. The third-party application can use Refresh Access Token to update the tokens, or use the Get Access Token to request new access token and refresh token.